Amazon EC2, a widely utilized AWS service, offers a VPS under the IaaS model. Its robust EC2 security features, coupled with complete server control and flexible pricing plans, make it highly attractive for companies managing their IT infrastructure.
However as the organizations rely on EC2 instances to run critical applications and services, it becomes imperative to emphasize the significance of proper security implementation.
In this article, we will walk you through the tools AWS provide and the best practices when using EC2 instance.
EC2 Security Groups
Security Groups in EC2 are virtual firewalls that control the inbound and outbound traffic to and from your EC2 instances. As most of the work is related to in/out traffic. Being able to control what can enter and what can leave the server is important.
Creating a Security Group
When you create an EC2 instance you will be asked to create or add an existing security group to the instance. But let’s see how to create it without creating the EC2, and attaching it to the EC2 instance.
Login to your AWS console and navigate to the EC2 dashboard. Select the Security Groups option from the “Network & Security”.
It will show you all the existing security groups.
To create a new security group click on the “Create security group” button from the top right corner.
And you will be taken to the security group setup page.
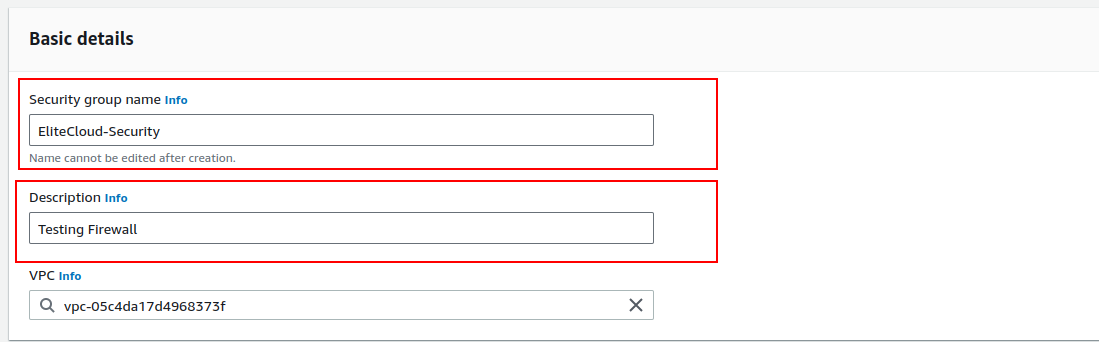
Fill in the name and description make sure to choose the name you want because you won’t be able to edit it later. But you can always create a new group if you want.
Then there’s the inbound rule section.
What are Inbound rules?
Inbound rules control incoming traffic to your EC2 instances. This lets you select the IP address that can connect to your EC2 instance you can also specify the port number and service where you want to allow the traffic. E.g. creating a rule to allow SSH access on port 22 from a specific IP.
Let’s create three inbound rules that allow the protocol SSH (22), HTTP (80), and HTTPS (443) to connect to the EC2 instances of that security group. You can do this by clicking the “Add rule” button.
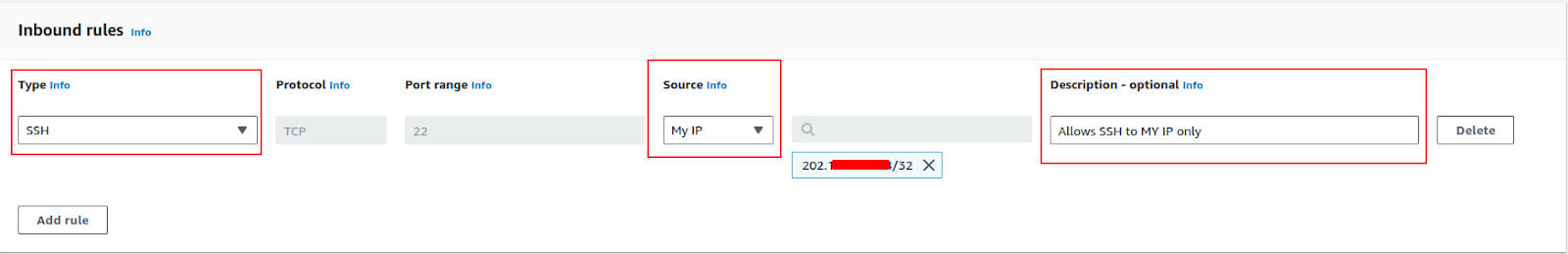
Here you will have to select the type that has predefined values, like SSH or HTTP will automatically select the protocol and ports that default to the service. But you can choose a different port by selecting custom TCP/UDP.
Next the “Source” will let you select the IP or IP ranges from where you want to allow traffic. In this case, I’m using my IP only.
Then there’s the optional description, you can write the reason for that rule here.
Once all is done, click “Add rule” and it will create an inbound rule. You can follow the same process to create more rules.
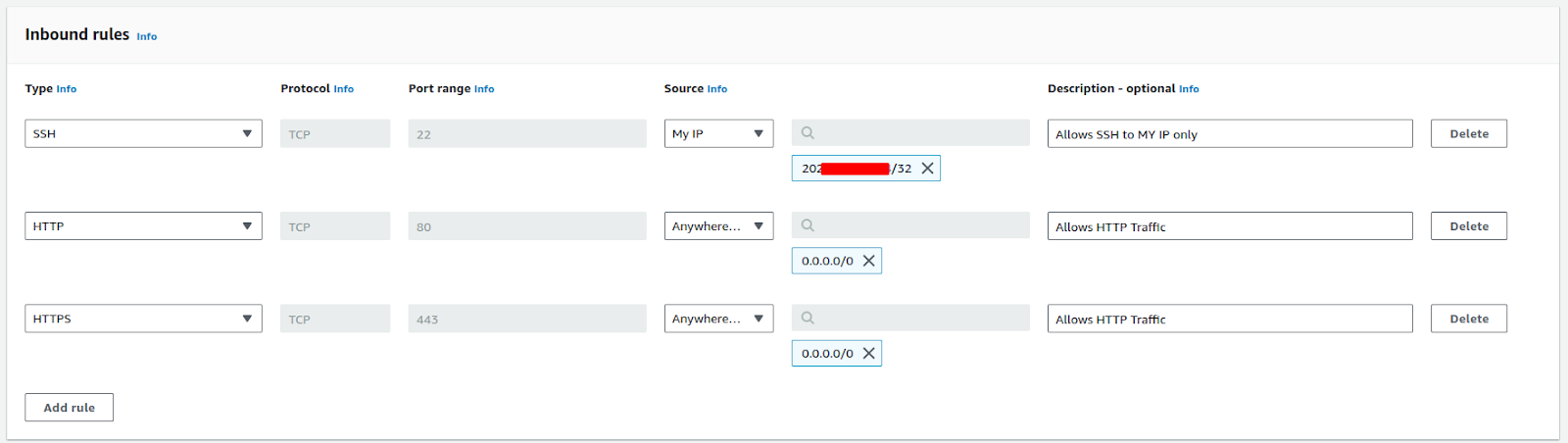
When you allow incoming traffic from all IPs, it’s best that you know what you’re doing.
Next, we have to select the Outbound rules.
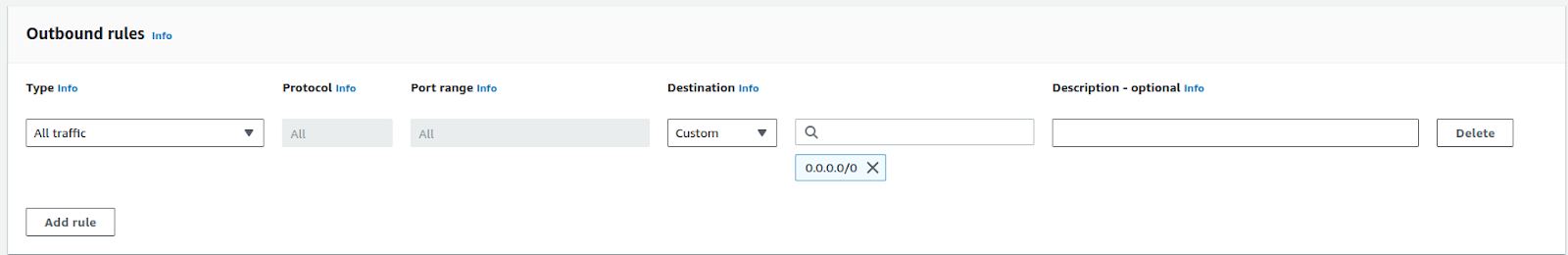
What are Outbound rules?
These Outbound rules control outgoing traffic from your EC2 instance to the internet. You can select which of your services will be exposed to the internet using these rules. This is very important to understand. Because a VPS mostly contains both private and public services. You don’t want your private service to be exposed to the internet. One of the examples is the internal database. If exposed to the internet will cause extra problems for your team to handle.
With that said let’s allow all traffic as we don’t have any private service active in the EC2 instance that we will connect.
Just click the “Add rule” button keeping everything default.
You can choose optional Tags to explain your resources better.
Once done, click “Create security group” This will create a security group for you.
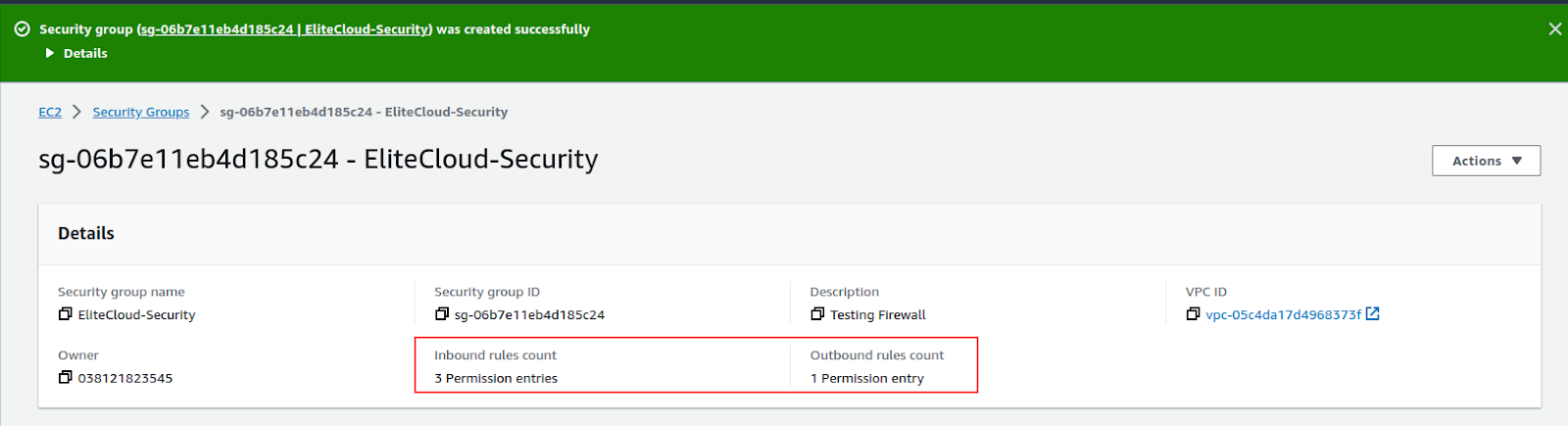
Now you can attach it to any EC2 instance you like and the permission will be applied to the instance you select.
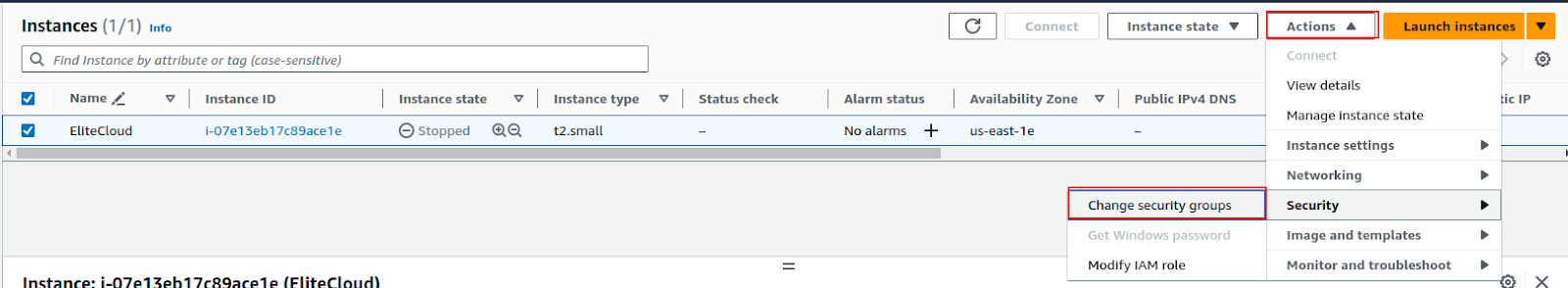
To add a security group to an instance select the instance and click “Actions > Security > Change security groups”.
This will take you to a new page, from the search bar select the security group of your choice and click “Add security group”.
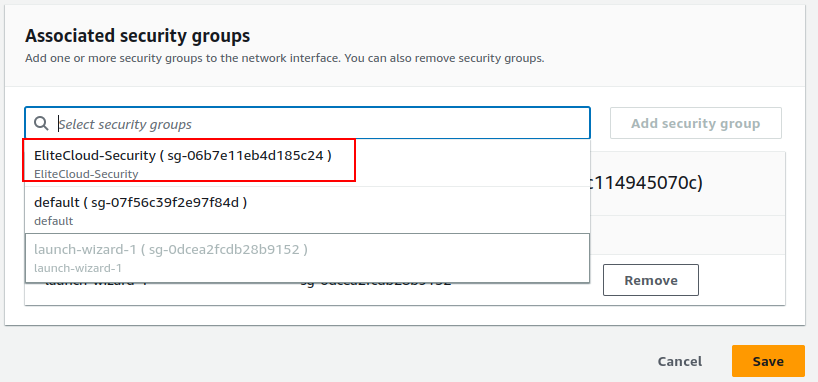
You can also remove any previously added security groups if you want to.
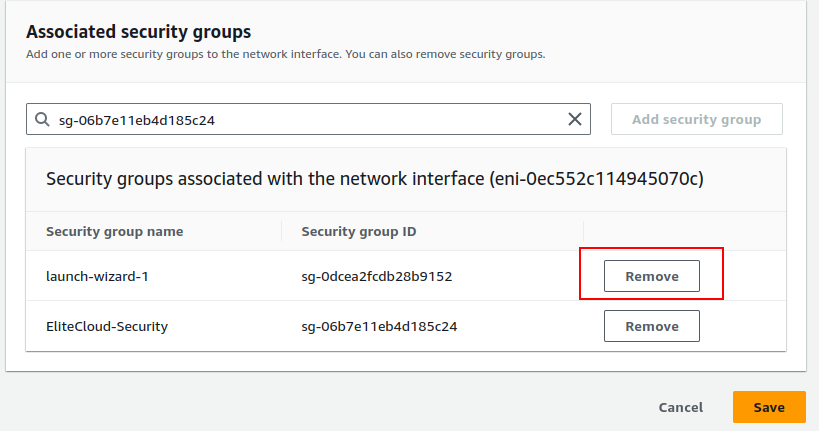
Once you are done click save and your security group for the selected instance will be updated.
You can check it from the security group and see all the inbound and outbound rules.
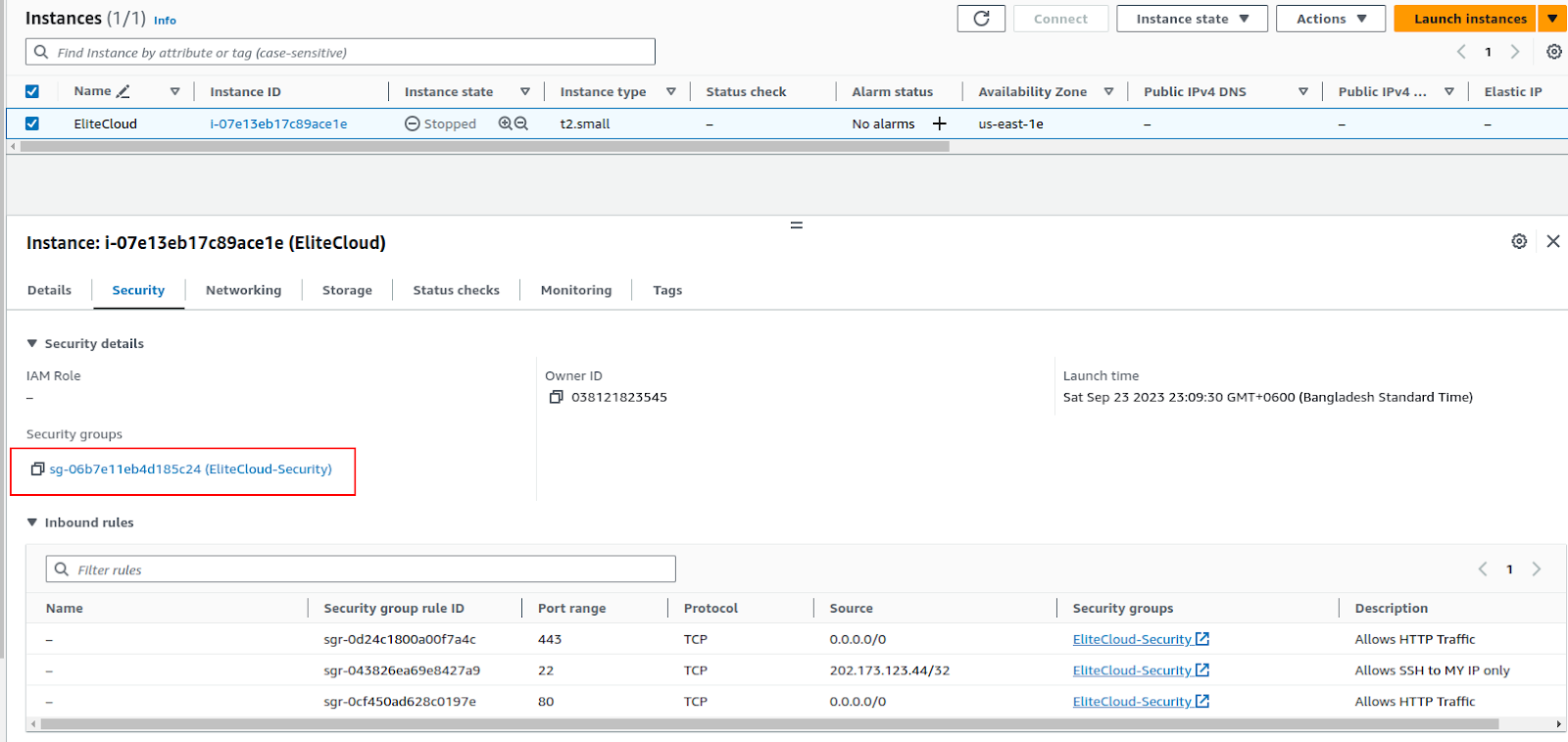
You can also add and modify the security group to add or remove new security rules.
Key Pair Management
Key Pair is the cryptographic key that allows only authorized people to access your AWS resources. A key pair has a public key and a private key, where the public key is used for encryption and the private key for decryption. This feature is used to login into SSH for linux and RDP for Windows EC2 instances.
While key pair gives you secure access to your instance. If it falls to the wrong hand it may lead to a complete compromise of your EC2 instance.
Creating Key Pair in EC2
When you create an EC2 instance you will be asked to create/select a key pair. But you can also create it after you’ve created an instance. And then assign it to a specific instance. Although it’s best to create a key pair before ahead. Because replacing a key pair is not as easy as it was with security groups.
From the EC2 dashboard go to “Network & Security > Key Pairs”.
This is where you can see all the keys available for your EC2 instances.
Click the “Create key pair” button to create a new key pair.
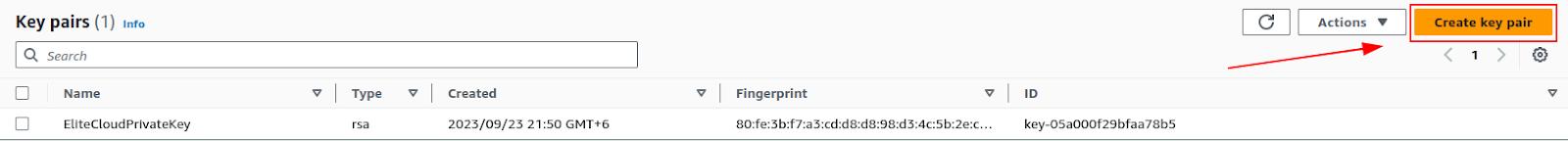
Note: You mustn’t delete the old key pair unless you’ve attached the new key pair.
This will take you to the setup page.
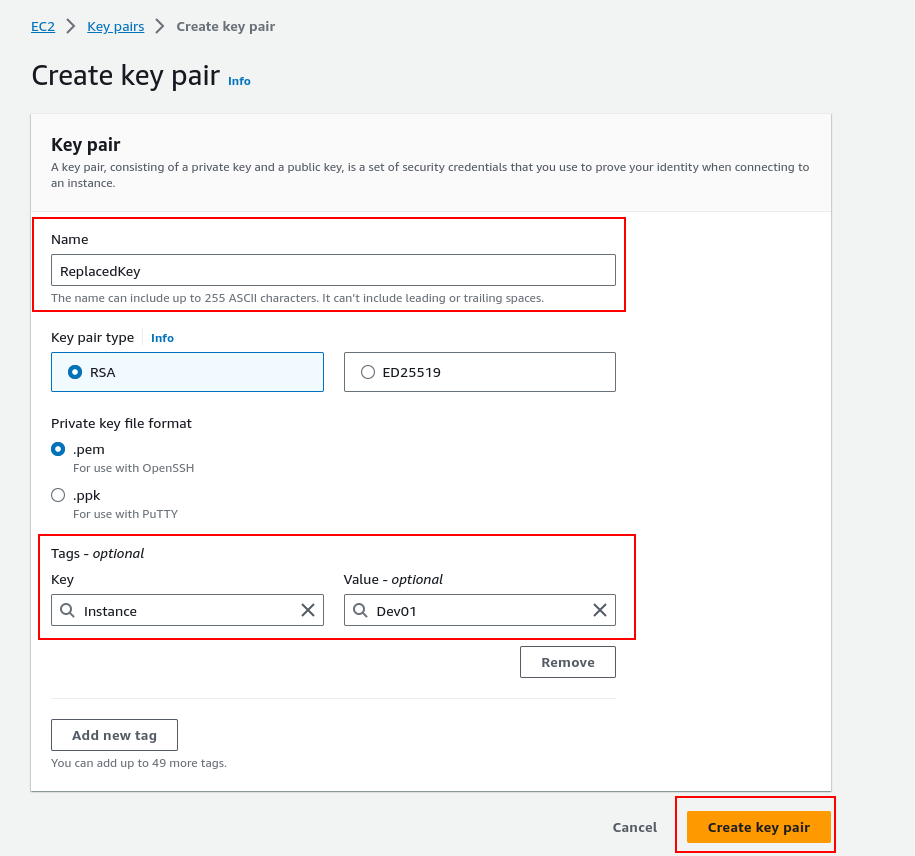
Fill in the Name and Tags and keep everything default. You can change the “Private key file format” to ppk if you are using putty.
Once you are done filling in the info, click “Create key pair”.
This will create a new key pair and download the private key (keyname.pem) in your system.
Replacing the Old Key Pair
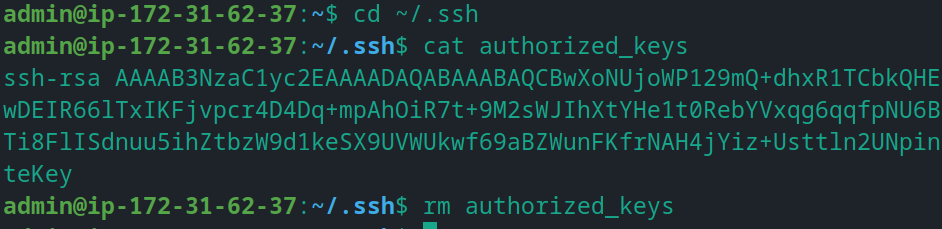
First login to your EC2 instance using the previous key pair. Navigate to the directory “~/.ssh/”. You will find the public key in the “authorized_keys” file. Now remove the “authorized_keys” file because we will replace it with new keys.
Alert: Please only do this when you know what you are doing.
Once done, navigate to your terminal (different one) where you have downloaded the new Private Key. Execute the command “chmod 400 ReplacedKey.pem” (change the filename). Then execute “ssh-keygen -y -f ReplacedKey.pem” (also change the name). This will generate a new public key from that private key.
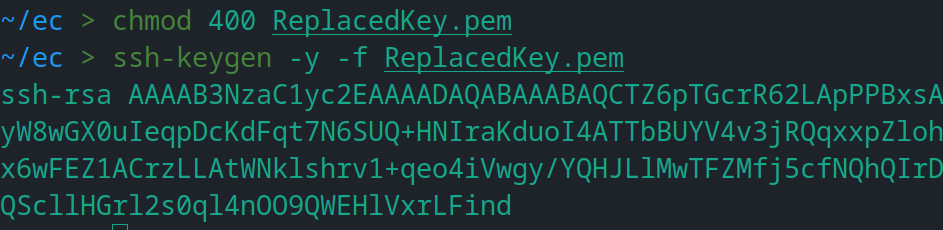
Now all you have to do is create a new “authorized_keys” file and copy the generated public key there. You can do this using echo or any text editor of your choice.
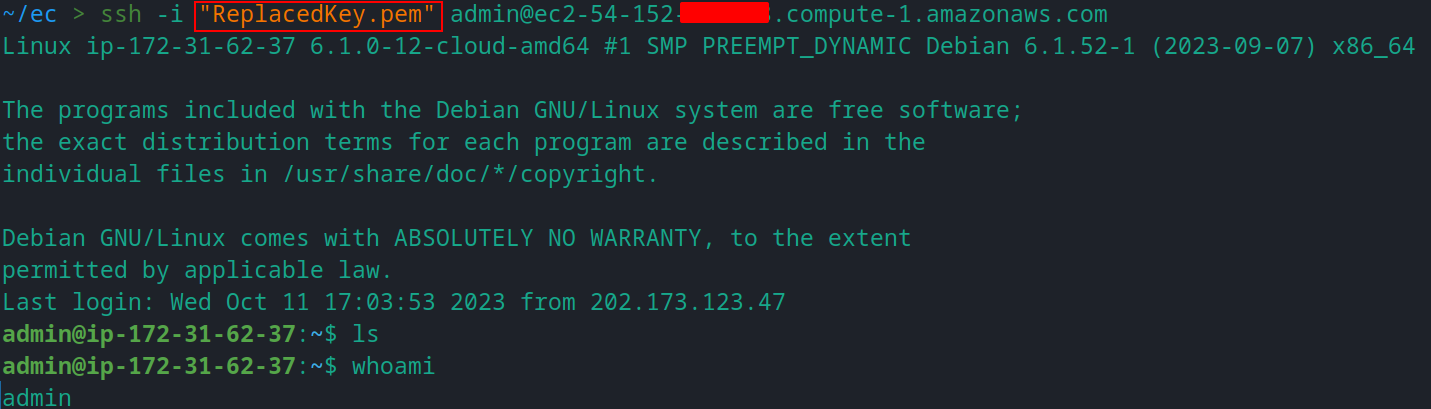
Please recheck that the key file is there and you’ve put the correct key. Now exit from your instance and reboot the EC2 instance (Reboot is optional in this case).
Now try to log in with the new private key and if everything is done correctly you will be successfully logged in.
Follow this doc to learn more about replacing key pairs.
Key Pair Best Practices
- Never share your private key unless you know what you are doing.
- Keep your private key in a safe place. Don’t put it in public SharePoint.
- Rotate Key Pairs (This one is specific to company policy).
- Monitor Key Pair Usage.
Multi-Factor Authentication (MFA)
Multi-factor authentication allows you to securely log into your EC2 instance. It adds an extra layer of security. After you log in using the private key you will have to enter an OTP to log in. You can set up this OTP using an Authenticator App like Google Authenticator.
This approach is only recommended when you know how to set it properly. We will bring a dedicated article on how to use MFA in EC2 instances.
Security through IAM
Identity and Access Management (IAM) is an AWS service that lets you manage the permissions of your AWS resources including EC2. With this, you can limit the interaction with EC2 to only the required permission. There are more than 39 policies only for EC2-related tasks, including EC2 Full Access, EC2 Read-Only Access, EC2 Start and Stop Instances, and more.
IAM follows the principle of least privilege meaning allowing only the permission that is required to perform the task. You can also use MFA for an IAM account. But we will have a different article for that.
Check out this article to learn more about IAM and its usage.
Conclusion
In this article, we’ve highlighted the EC2 security group, Key Pair, MFA, and IAM. But EC2 security is not limited to those 4 components. You should build your cloud infrastructure with proper security in place to avoid the worst reality.

